Bip39 Passphrase, what is it and how does it work?
Just run a script to see how seed is calculated from mnemonic in the BIP39 standard
Bip39 Passphrase?
What is the BIP39 passphrase? The answer to this question is still not clear to many people willing to configure and put in security their hardware device for hodling their loved bitcoin.
As you can read everywhere, a new BIP39 passphrase, applied to your existing 12/24 mnemonic words, returns a totally different wallet (seed). So you can have many different wallets just changing the BIP39 passphrase to your existing mnemonic words.
This can lead to many advantages, for example the possibility to create different Wallet (for example for accounting reasons or for hiding reasons) without having to define new different mnemonic words. So a good amount of security without a great increase in complexity.
But in order to use this tool properly, you should understand what exactly this means. Infact the phrase
“..returns a totally different wallet (seed)..”
is in many case still undefined or misunderstood until you see how the seed is actually formed. So checkout second part of this article about how to calculate it
Calculating the seed from the mnemonic
Let’s imagine to have this valid BIP39 12 words mnemonic
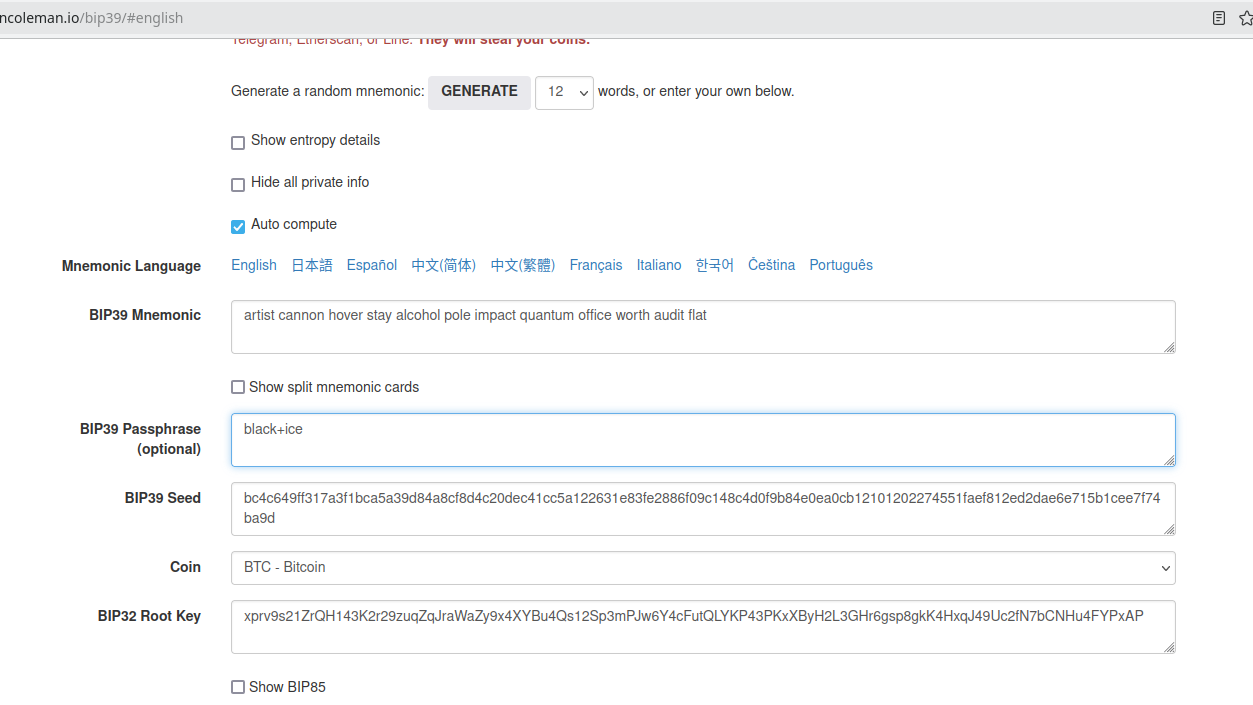
artist cannon hover stay alcohol pole impact quantum office worth audit flat
Now let’s use phpcli for this calculation, and this is what we get, using the interactive shell:
massmux@tiberius:~$ php -a
Interactive shell
php > echo hash_pbkdf2("sha512", "artist cannon hover stay alcohol pole impact quantum office worth audit flat", "mnemonic", 2048);
3a94ee768d1d07df4feb506c5ca0f9da927e7926a1a0bd7f345c5ffce6b5a8c18631837fcda9e916552e3b539fd5348bb1e9b22653543d78d6a793c25d55bf48
So we used the word “mnemonic” as standard salt for this calc. Infact when no passphrase is specified, the word “mnemonic” is used as a salt, as specified by BIP39 standard. More info on this link: https://github.com/bitcoin/bips/blob/master/bip-0039.mediawiki
For this reason in the above calc we used “mnemonic” as a salt. The iteration count is set to 2048 and HMAC-SHA512 is used as the pseudo-random function. The length of the derived key is 512 bits (= 64 bytes).
If we check on Ian coleman tool we can see
It’s easy to check that the resulting BIP39 seed is matching with our calculation. So that’s ok.
Now let’s try to do the same with Python code. Here we go
from hashlib import pbkdf2_hmac
iterations = 2048
passphrase_string="mnemonic"
salt = bytes(passphrase_string,'utf-8')
mnemonictohash = 'artist cannon hover stay alcohol pole impact quantum office worth audit flat'
hash = pbkdf2_hmac('sha512',bytes(mnemonictohash,'utf-8'), salt, iterations, dklen=64)
print(f"pbkdf2:{iterations}:{salt.hex()}:{hash.hex()}")
if we run this code we get
pbkdf2:2048:6d6e656d6f6e6963:3a94ee768d1d07df4feb506c5ca0f9da927e7926a1a0bd7f345c5ffce6b5a8c18631837fcda9e916552e3b539fd5348bb1e9b22653543d78d6a793c25d55bf48
in particular
3a94ee768d1d07df4feb506c5ca0f9da927e7926a1a0bd7f345c5ffce6b5a8c18631837fcda9e916552e3b539fd5348bb1e9b22653543d78d6a793c25d55bf48
is the expected seed.
Adding a passphrase
Now let’s use the same code to add a passphrase. By the BIP39 specifications, the passphrase string should be a whatever string which will be concatenated to “mnemonic”. So imagine our passphrase is
black+ice
then the string which will be used as a salt will be
mnemonicblack+ice
in the code above we have to set
mnemonic_string="mnemonicblack+ice"
then we can run again the script. We get this seed
bc4c649ff317a3f1bca5a39d84a8cf8d4c20dec41cc5a122631e83fe2886f09c148c4d0f9b84e0ea0cb12101202274551faef812ed2dae6e715b1cee7f74ba9d
check it on Ian Coleman
once again, all is matching. Being 2 different seeds, this means we have actually 2 different Wallets (with different addresses, keys, etc). The Passphrase can be whatever string, it does not matter. You can decide how to specify it and the level of complexity you want to achieve.
So now it should be clear what BIP39 passphrase is and how it is actually calculated. Enjoy!
Dont forget to subscribe this newsletter for FREE in order to get informations, snippets, code and more for your preferred technologies.




Ciao
Great, very clear, thanks a lot!